How to Upskill IT Teams for Zero Trust
Zero Trust security is all about one principle: never trust, always verify. This approach ensures every access request is authenticated and authorized, regardless of its origin. Shifting to Zero Trust requires more than just tools – it demands new skills across IT teams to protect identities, devices, data, and networks effectively.
Key Takeaways:
- Core Principles of Zero Trust: Verify explicitly, use least privilege access, and assume breach.
- Why Training Matters: IT teams must handle multi-cloud setups, edge computing, and IoT, which expand attack surfaces.
- Roles Needed: Security architects, identity admins, network engineers, and more.
- Skills to Build: Microsegmentation, identity management, real-time monitoring, and advanced incident response.
- Training Roadmap: Start with basics, move to hands-on labs, and progress to advanced role-specific training.
- Practical Steps: Use tools like Microsoft Entra or CISA resources, conduct regular drills, and leverage isolated staging environments for testing.
Upskilling IT teams for Zero Trust ensures stronger security against modern threats while enabling them to manage complex infrastructures confidently.
Implementing Zero Trust Architecture: A Step-by-Step Guide Part 1
Finding Roles and Skill Gaps for Zero Trust
Zero Trust Team Roles and Required Skills Framework
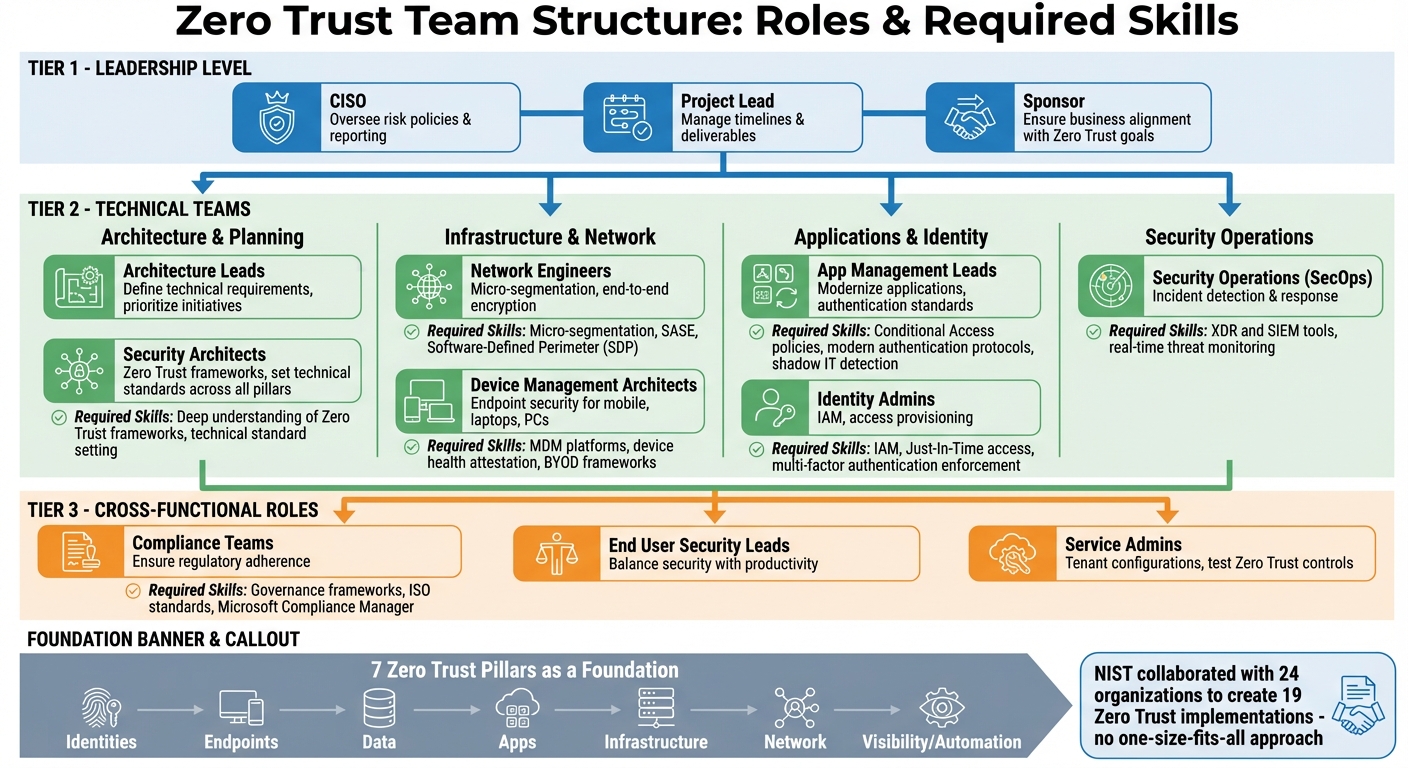
Building a Zero Trust framework isn’t something one person can tackle alone. It calls for a well-coordinated team effort, with clearly defined roles and a sharp eye on where skills might be missing. The first step? Identifying the crucial roles needed and aligning them with the core pillars of Zero Trust.
Key Roles in Zero Trust Operations
Zero Trust revolves around seven core pillars: Identities, Endpoints, Data, Apps, Infrastructure, Network, and Visibility/Automation. Each of these areas demands specialized knowledge, so your team structure should reflect this diversity.
At the leadership level, you’ll need a CISO to oversee risk policies and reporting, a Project Lead to manage timelines and deliverables, and a Sponsor to ensure the business stays aligned with Zero Trust goals. These roles are vital for setting the strategy and keeping executive support intact throughout the process.
On the technical side, the heavy lifting falls to architects and operational teams. Architecture Leads define the technical requirements and prioritize key initiatives. Device Management Architects focus on endpoint security for mobile devices, laptops, and PCs. Networking Teams take charge of micro-segmentation and implementing end-to-end encryption. Meanwhile, App Management Leads work on modernizing applications with updated authentication standards. Security Operations (SecOps) teams are tasked with detecting and responding to incidents, using tools like XDR and SIEM to monitor threats in real time.
Cross-functional roles are equally important. Compliance Teams ensure adherence to regulations, while End User Security Leads balance security measures with maintaining productivity. In hosting environments, Service Admins handle tenant configurations and test Zero Trust controls before deployment. If your organization uses Serverion hosting, make sure your Service Admins are well-versed in Zero Trust practices.
Required Skills for Each Role
Once roles are defined, it’s time to outline the technical expertise each one demands. For example:
- Network Engineers should be skilled in micro-segmentation, Secure Access Service Edge (SASE), and Software-Defined Perimeter (SDP) technologies.
- Identity Admins need a strong grasp of Identity and Access Management (IAM), Just-In-Time access provisioning, and enforcing multi-factor authentication.
- App Management Leads must understand Conditional Access policies, modern authentication protocols, and how to detect shadow IT.
Other roles require equally specific skills. Device Management Architects should be proficient in mobile device management (MDM) platforms, device health attestation, and securing BYOD frameworks. Security Architects must have a deep understanding of Zero Trust frameworks and the ability to set technical standards across all pillars. Compliance Teams should know governance frameworks, ISO standards, and tools like Microsoft Compliance Manager to track regulatory progress.
The NIST National Cybersecurity Center of Excellence has worked with 24 collaborators to create 19 Zero Trust implementations. This highlights an important point: there’s no one-size-fits-all skill set for Zero Trust.
How to Conduct a Skills Gap Analysis
Start by using a maturity model assessment. The CISA Zero Trust Maturity Model (ZTMM) Version 2.0 breaks implementation into five pillars: Identities, Devices, Networks, Applications and Workloads, and Data. This framework helps you evaluate where your team currently stands, ranging from "Traditional" (static security) to "Optimal" (fully automated and dynamic).
Tabletop exercises are another effective way to identify gaps. Simulate real-world scenarios – like authentication failures or data breaches – to uncover weaknesses in your team’s response. These exercises can pinpoint where cross-functional coordination needs improvement.
You can also rely on in-product dashboards to measure technical gaps. Tools like Microsoft Security Exposure Management allow you to capture baseline security scores and monitor progress over time. Hosting workshops focused on specific Zero Trust pillars is another useful strategy to identify key stakeholders and areas for improvement. To keep up with evolving threats, CISA suggests conducting these assessments every six months.
Finally, use the CISA Cybersecurity Workforce Training Guide to map your findings to a competency framework. This helps align skill requirements with specific roles and ensures accountability by assigning tasks to the right team members. By tracking these efforts, you can clearly see where expertise is lacking and who needs additional training to close the gaps.
Building a Training Roadmap for Zero Trust
Once you’ve identified the skills your team needs, the next step is creating a structured training program. This roadmap should guide your team from the basics to advanced practices, ensuring they develop the right skills at the right pace for their specific roles.
Tiered Learning Path for IT Teams
Begin with foundational training to cover the core principles of Zero Trust. At this stage, your team should gain an understanding of the seven key technology pillars: Identities, Endpoints, Data, Apps, Infrastructure, Network, and Visibility/Automation. Training modules from Microsoft and CISA are excellent resources for this foundational level.
Next, move to intermediate training, which should include scenario-based learning and hands-on labs. The Microsoft Zero Trust Lab Guide provides Level 200 training paths for Microsoft 365 and Azure. This stage emphasizes identity synchronization, device management using Intune, and cloud security benchmarks. The structured lab environment allows your team to build skills progressively.
Finally, in advanced training, focus on specialized technical implementations. This includes incident response using tools like XDR and SIEM (e.g., Microsoft Sentinel) and securing advanced workloads such as AI Copilots. CISA’s Cyber Storm exercises, which simulate large-scale attacks on critical infrastructure, are a great way to prepare for real-world scenarios. To ensure smooth progression, establish clear criteria for moving between these levels.
This tiered approach creates a strong foundation for tailoring training to specific roles.
Role-Based Training Plans
Once the roadmap is in place, align training to the responsibilities of different roles:
- Security Architects should focus on adoption frameworks, strategic planning, and designing architecture across all seven pillars.
- IT Implementers need technical training, including pillar-specific checklists and configuration guidance for deployment.
- Teams managing Microsoft 365 environments should prioritize training on Microsoft Entra, Intune, and Purview.
For Application Developers, training should emphasize Security by Design – building applications with secure identity permissions, proper consent, and secure DevOps practices. Security Operations Analysts should focus on the Visibility, Automation, and Orchestration pillar, with training on integrating XDR and SIEM tools. Network Engineers will benefit from specialized training in micro-segmentation, real-time threat protection, and end-to-end encryption. Microsoft also offers deployment training in five "swim lanes", such as "Secure remote and hybrid work", to help teams address specific business needs.
Using External Training Resources
External training platforms can be a valuable addition to your roadmap, offering a range of options to deepen your team’s expertise.
- CISA Learning provides free, on-demand cybersecurity training for federal employees, private-sector professionals, and the public. Their Federal Cyber Defense Skilling Academy is a 12-week program designed to build foundational skills for Cyber Defense Analysts.
- Fortinet Training Institute offers free self-paced advanced training, with tracks for Zero Trust Network Access (ZTNA) and Secure Access Service Edge (SASE). Their Network Security Expert (NSE) certifications count toward ISC2 Continuing Professional Education (CPE) credits and can also help renew certifications like CompTIA Security+, Network+, and CySA+.
- Microsoft Learn features free self-paced modules covering identity, Microsoft 365/Azure deployment, and security architecture. While certification exams usually have a fee, these modules are a great starting point.
Before diving into any training, use tools like the Microsoft Zero Trust Security Posture Assessment to evaluate your team’s current maturity level. This ensures you’re choosing the right paths to address gaps effectively.
sbb-itb-59e1987
Hands-On Labs and Practice
Once structured training is complete, hands-on labs become essential for solidifying Zero Trust expertise. These labs and simulations provide a safe space for your team to experiment with Zero Trust policies, turning potential mistakes into valuable learning moments rather than costly security incidents. This approach bridges the gap between theoretical knowledge and practical application.
Designing Progressive Lab Scenarios
Effective lab scenarios should revolve around the core pillars of Zero Trust: identity, endpoints, data, applications, infrastructure, and network. Start with foundational tasks, such as verifying identity and checking device compliance, then move on to more advanced exercises like micro-segmentation and anomaly detection.
Take Zscaler’s Zero Trust Cloud Self-Guided Lab (introduced in 2024/2025) as an example. This lab includes targeted modules where teams can practice enforcing minimum TLS versions to secure workloads, set up Data Loss Prevention (DLP) policies, configure Zero Trust Gateways, and utilize AWS tagging for precise policy enforcement.
Similarly, researchers at NIST have developed a robust Zero Trust Architecture Project. Their testing scenarios include toggling resources and endpoints between on-premises and internet-based locations. They also simulate situations where users or devices are intentionally misconfigured as "unauthorized" or "non-compliant", ensuring the Policy Enforcement Point (PEP) properly denies access.
When designing your own scenarios, aim to test multiple variables simultaneously. This helps replicate real-world complexities and allows your team to understand the implications of policy adjustments before rolling them out in production.
Using Staging Environments Safely
Staging environments are a critical component of safely testing Zero Trust policies. By leveraging tools like Serverion’s VPS and dedicated servers, you can create isolated spaces for experimenting with access controls, network segmentation, and security policies without risking disruptions to your live systems.
These environments allow you to observe normal traffic patterns before enforcing new policies, reducing the risk of creating overly restrictive rules that could hinder business operations. Microsegmentation can further enhance safety by isolating the training environment from production systems, preventing lateral movement and containing any potential issues within the lab.
"OT environments are so sensitive that many tools need to be passive to avoid the risk of accidentally causing disruptions." – Imran Umar, Cyber Leader, Booz Allen Hamilton
For legacy systems, consider using an overlay approach. This involves creating an identity for assets and enforcing access controls through a proxy, avoiding direct modifications to the assets themselves. Mapping transaction flows beforehand can also help identify how data interacts with various systems and uncover potential vulnerabilities.
Running Drills and Incident Simulations
Regular drills are essential for preparing your team to handle real-world Zero Trust incidents. Focus on scenarios that test critical areas like access control, device integrity, network security, data protection, and cloud infrastructure. For example, simulate situations where unauthorized access is attempted, unmanaged devices request resources, or services try to communicate laterally across your network.
These drills should also include testing defenses against threats like malicious payloads, phishing attempts, and botnet activity. Practice responding to DLP triggers and scenarios where sensitive data is moved to unauthorized locations. Behavioral anomaly detection exercises are particularly useful for preparing your team to deal with zero-day attacks that lack known signatures.
Run these drills every six months to measure progress and refine your security strategies. Develop a comprehensive suite of tests to validate your Zero Trust Architecture before and after rolling out new features or capabilities. Use discovery tools to monitor transaction flows and ensure your enforced policies align with your organizational rules.
Investing in regular incident response testing pays off significantly. Organizations with well-tested response plans save an average of $2.66 million per breach, making this a crucial step in strengthening your security posture.
Integrating Zero Trust into IT Operations
Once your team has completed training and hands-on labs, the next step is weaving Zero Trust into your daily IT workflows. This means shifting security from being an isolated function to a shared responsibility that involves leadership at the executive level. Updating standard procedures to include Zero Trust principles is a critical part of this transformation.
Adding Zero Trust to Standard Operating Procedures
To embed Zero Trust into your operations, start by revising your standard operating procedures. Every stage – whether it’s system onboarding, deployment, or change management – should integrate key Zero Trust elements like identity verification, device compliance checks, and least-privilege access controls. A helpful resource for this process is CISA’s Zero Trust Maturity Model Version 2.0, which provides a structured framework organized across five pillars and three cross-cutting capabilities.
Adopt a repeatable cycle that includes strategy, planning, readiness, adoption, and governance. This approach shifts your focus from reactive responses to proactive measures, such as just-in-time access and strict adherence to least-privilege principles.
Instead of overhauling everything at once, implement Zero Trust in phases. Start with specific areas of your digital infrastructure, prioritizing zones where the risk of data loss, leakage, or compliance failure is highest. Avoid disruptions by documenting responses to critical issues like authentication failures or tenant lockouts to ensure business continuity as you make the transition.
"Security is a responsibility shared among all levels of the business. Accountability for security rests with the executive, while responsibility is shared using the three Zero Trust principles of Assume breach, Verify explicitly, and Use least privilege access." – Microsoft
Maintaining Skills Through Continuous Learning
To keep Zero Trust skills sharp, schedule quarterly 15-minute tabletop exercises that simulate real-world incident scenarios. These exercises, like those provided by the CIS Six Tabletop Exercises, help teams identify gaps in workflows and strengthen their ability to respond to threats.
Use systematic tools like Microsoft Security Exposure Management or Excel-based assessment workbooks to track progress. These tools assign ownership, set measurable objectives, and provide metrics that align with other operational health indicators. Behavioral analytics can also help you spot anomalies and refine your security posture.
Regular red and blue team exercises are another essential practice. Test your defenses in areas like access control, device integrity, network security, and data protection. These exercises not only reinforce incident response readiness but also ensure that your policies remain aligned with your organization’s evolving needs. Continuous testing and learning prepare your team to seamlessly integrate Zero Trust into all aspects of IT operations.
Using Hosting Platforms for Zero Trust
Hosting platforms play a key role in implementing Zero Trust by offering secure, isolated environments for testing and deployment. For example, Serverion’s VPS and dedicated servers provide the isolation needed to test access controls and network segmentation without jeopardizing production systems. These platforms also handle some maintenance responsibilities, easing the burden on your team.
When modernizing legacy applications, consider moving to trusted hosting providers. This transition raises the "attacker’s cost", making your organization a less appealing target. Serverion’s infrastructure, which spans multiple global data centers, supports microsegmentation strategies and offers a secure foundation for Zero Trust operations. Their services, such as SSL certificates and server management, enable IT teams to enforce detailed access controls while maintaining performance and reliability.
Leverage in-product dashboards and security metrics from your hosting platform to monitor your Zero Trust implementation. This ensures that as your team’s expertise grows, your infrastructure evolves to support more advanced Zero Trust strategies. By combining skill development with robust hosting solutions, you can build a resilient and secure IT environment.
Conclusion
Continuous improvement is the backbone of effectively upskilling your IT team for Zero Trust. This journey isn’t a one-time effort – it’s an ongoing process that reshapes how your organization approaches security. Start by identifying where skill gaps exist across critical roles, and craft a structured training plan that blends role-specific learning with hands-on experience. A phased approach works best: begin with straightforward steps like implementing Multi-Factor Authentication, then gradually move toward advanced techniques like refined network segmentation.
The turning point comes when Zero Trust principles become second nature in everyday operations. This means updating procedures to include identity verification, ensuring device compliance, enforcing least-privilege access, and running regular drills to identify and address vulnerabilities. Incorporating tabletop exercises and red/blue team drills keeps your team sharp and ensures skills remain relevant.
"By building a foundation of IT professionals who understand and embrace ZT principles, you are greatly improving your chance of success." – Federal ZT partner
The most successful Zero Trust strategies are marked by a commitment to ongoing learning. Use maturity models and scoring systems to track progress, and help your leadership team see how Zero Trust transforms security from a cost center into a strategic growth enabler. Investing in training doesn’t just reduce risks – it raises the bar for attackers, making your organization a tougher target.
Platforms like Serverion offer secure hosting environments that provide the infrastructure your team needs to implement and refine Zero Trust strategies. With robust features and a secure foundation, your team can focus on mastering Zero Trust principles. As your team’s expertise grows, your infrastructure should evolve alongside it, ensuring your security posture remains resilient and adaptable to new threats. By integrating these efforts, Zero Trust becomes the cornerstone of your long-term security strategy.
FAQs
What key roles are essential for successfully implementing Zero Trust?
Implementing Zero Trust successfully involves teamwork across various IT roles, each contributing their expertise to build a secure system. Here are the key roles typically involved:
- Security Architects: These professionals design and oversee the Zero Trust framework, ensuring it aligns with the organization’s objectives and security needs.
- Network Engineers: They configure and manage the network infrastructure to ensure it supports the policies and principles of Zero Trust.
- Identity and Access Management (IAM) Specialists: Focused on user authentication and access controls, they manage the systems that verify identities and enforce permissions.
- Endpoint Security Experts: Responsible for monitoring and securing devices that connect to the network, ensuring every endpoint adheres to security protocols.
Each role is vital in building and maintaining a Zero Trust architecture that meets modern security demands. Investing in training and skill development for your team in these areas can make all the difference in achieving a robust implementation.
How can IT teams identify and address skill gaps for implementing Zero Trust?
To address skill gaps in Zero Trust, start by assessing your IT team’s current strengths and weaknesses. Use established frameworks like maturity models to evaluate key areas such as identity management, device security, and risk-based access controls. Combine these with internal metrics – like response times or error rates – to pinpoint areas needing improvement.
Once you’ve identified the gaps, focus on targeted skill-building. Encourage your team to dive into core Zero Trust principles, including identity-centric security, micro-segmentation, and secure-by-design architecture. Certification programs and hands-on labs are great tools for developing these skills. Incorporating Zero Trust practices into daily tasks and cross-functional projects also reinforces learning through practical experience.
If your organization relies on Serverion hosting solutions, make sure your team applies Zero Trust strategies, such as least-privilege access and secure network segmentation, when managing critical workloads. Ongoing training and regular practice will not only safeguard assets but also help uphold Serverion’s reputation for top-tier performance and security.
What are the best ways to integrate Zero Trust into daily IT operations?
To bring Zero Trust into your daily IT operations, start by setting clear security objectives that align with its core principles, like “verify explicitly” and “assume breach.” Begin with a detailed assessment of your current IT setup to spot gaps, identify high-value assets, and highlight areas needing stronger protection. Use this information to craft a phased implementation plan, focusing on critical workloads, assigning roles, and setting achievable timelines.
Start with the basics of Zero Trust by rolling out multi-factor authentication (MFA), device health checks, and micro-segmentation. Use automation for enforcing policies with tools like conditional access and identity-aware firewalls. Keep a close eye on your system through regular monitoring, employing risk-based analytics, and fine-tuning policies to tackle emerging threats.
In day-to-day operations, weave security into your workflows by enforcing least-privilege access, automating compliance checks, and embedding security into change management and DevOps processes. Invest in training your IT team on key areas like identity governance, secure configurations, and incident response. For a smoother transition, consider working with a provider like Serverion. They can help simplify the process by offering secure infrastructure with built-in MFA, network isolation, and 24/7 monitoring – giving you a solid starting point for your Zero Trust journey.







