Zero Trust Encryption: Role of PKI Standards
Zero Trust Architecture (ZTA) shifts security from network-based trust to identity-based verification. Its guiding principle? "Never trust, always verify." Public Key Infrastructure (PKI) is central to this approach, ensuring secure authentication, encryption, and data integrity.
Key Highlights:
- Zero Trust Principles: Verify every access request, enforce least privilege, and assume potential breaches.
- PKI’s Role: PKI enables identity verification using digital certificates, public-private key pairs, and Certificate Authorities (CAs).
- Standards for PKI in Zero Trust:
- TLS 1.3: Secures data in transit with faster handshakes and stronger encryption.
- ACME: Automates certificate management for scalability.
- CMP v3: Prepares for quantum threats with Key Encapsulation Mechanism (KEM).
- Delegated Credentials: Short-lived credentials enhance security.
- OAuth 2.0 & JWS: Strengthen authorization and authentication processes.
- Automation’s Importance: Manual certificate management risks outages and inefficiencies; automation ensures scalability and reliability.
With remote work, IoT growth, and cloud reliance, Zero Trust is becoming standard. PKI, combined with automation, MFA, and SSO, ensures secure, identity-focused access in this evolving landscape.
Public Key Infrastructure: The Foundation of Digital Trust
PKI Standards for Zero Trust Encryption
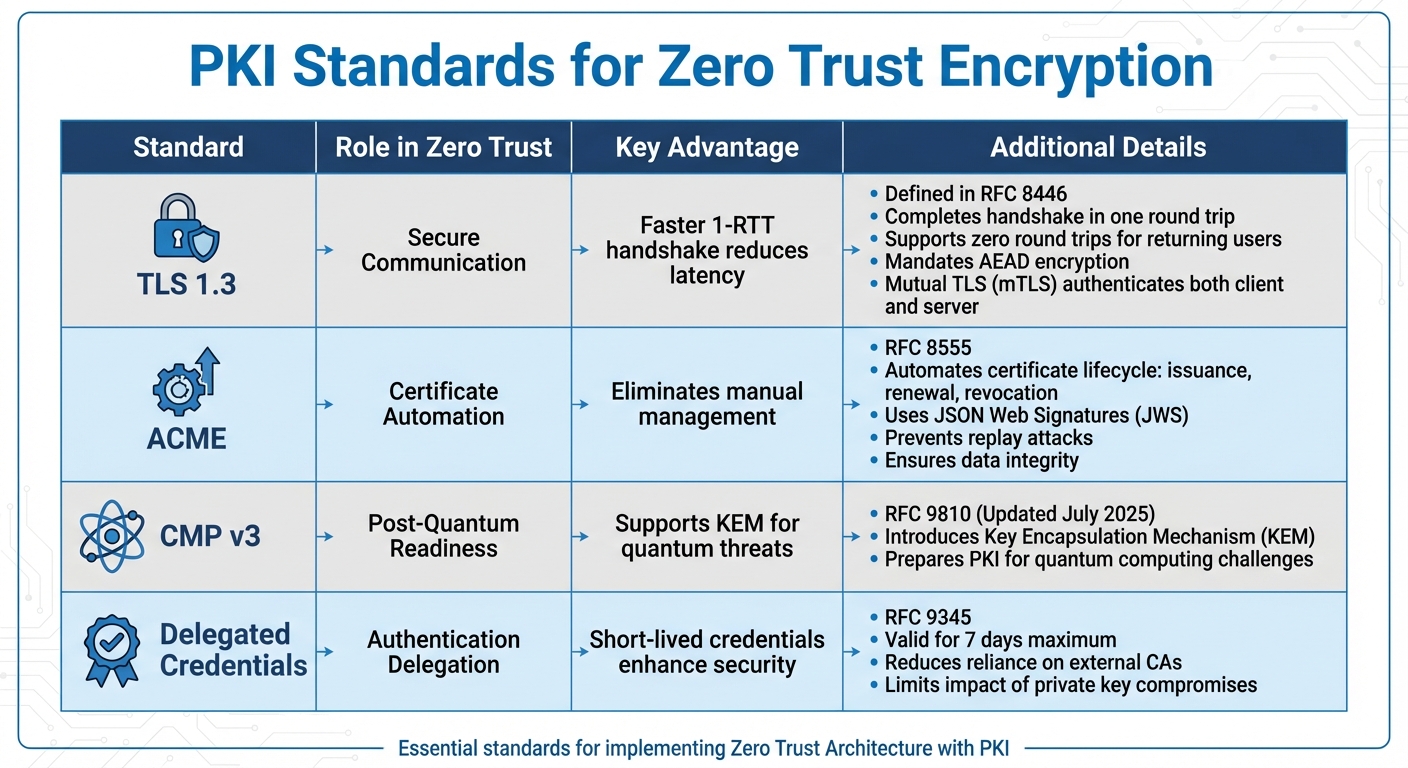
PKI Standards Comparison for Zero Trust Architecture
Public Key Infrastructure (PKI) plays a critical role in supporting Zero Trust principles. However, to ensure Zero Trust operates effectively, specific standards must be followed. These standards outline how devices and users verify their identities, how data is encrypted, and how certificates are managed at scale. Without these guidelines, Zero Trust implementations can become inconsistent and ineffective.
TLS/SSL Protocols for Secure Communications
TLS 1.3 (defined in RFC 8446) is pivotal for securing data in transit. It provides three essential security functions: encryption (to protect information from unauthorized access), authentication (to confirm the identities of communicating parties), and integrity (to ensure data remains untampered during transmission).
Compared to TLS 1.2, TLS 1.3 offers faster performance in Zero Trust setups by completing its handshake in just one round trip, with the added benefit of supporting zero round trips for returning users. It also encrypts handshake messages earlier in the process and removes outdated, weaker algorithms by mandating AEAD encryption. In Zero Trust environments, mutual TLS (mTLS) takes security a step further by authenticating both the client and server before any data is exchanged – an essential step to maintain trust.
Certificate Automation: ACME, CMP, and Delegated Credentials
Managing certificates manually is impractical in large-scale systems, which is why automation protocols are critical for Zero Trust PKI management.
- ACME (Automated Certificate Management Environment, RFC 8555): This protocol automates the entire lifecycle of certificates, from issuance to renewal and revocation, without requiring manual intervention. It uses JSON Web Signatures (JWS) to authenticate requests, prevent replay attacks, and ensure data integrity, aligning perfectly with Zero Trust principles.
- CMP (Certificate Management Protocol) Version 3 (RFC 9810): Updated in July 2025, this protocol introduces Key Encapsulation Mechanism (KEM) support, preparing PKI systems for the challenges posed by quantum computing.
- Delegated Credentials (RFC 9345): This standard allows server operators to issue short-lived credentials (valid for seven days) under a Certificate Authority (CA) certificate. By reducing reliance on external CAs for frequent renewals and limiting the impact of private key compromises, it enhances security in Zero Trust frameworks.
Authorization and Authentication Standards
Encryption alone isn’t enough for Zero Trust. Strong authorization and authentication standards are necessary to control access to resources securely.
- OAuth 2.0: This standard facilitates authorization by enabling systems to grant restricted access without sharing sensitive credentials like passwords.
- JSON Web Signature (JWS): JWS ensures the authenticity and integrity of request payloads, playing a key role in verifying communications.
- Authority Token Challenges (RFC 9447): This extension of ACME enables certificate issuance for non-Internet resources (like telephone numbers) by consulting an external Token Authority. It broadens the application of Zero Trust principles beyond traditional DNS-based validations.
| Standard | Role in Zero Trust | Key Advantage |
|---|---|---|
| TLS 1.3 | Secure Communication | Faster 1-RTT handshake reduces latency |
| ACME | Certificate Automation | Eliminates manual management |
| CMP v3 | Post-Quantum Readiness | Supports KEM for quantum threats |
| Delegated Credentials | Authentication Delegation | Short-lived credentials enhance security |
How to Implement PKI in Zero Trust Frameworks
Authenticating Users and Devices with PKI
Zero Trust operates on a simple but powerful principle: no entity is trusted by default. Every user, device, or service must prove its identity before accessing resources. Public Key Infrastructure (PKI) provides the cryptographic backbone for this, issuing digital certificates that act as unique, verifiable identifiers.
"A key paradigm shift in ZTAs is the change in focus from security controls based on segmentation and isolation using network parameters (e.g., Internet Protocol (IP) addresses, subnets, perimeter) to identities." – Ramaswamy Chandramouli, NIST
To align with this shift, authentication and authorization should be treated as separate processes. PKI ensures that every access request is verified, regardless of whether the request originates inside or outside traditional network boundaries. This is especially crucial for hybrid workforces and "bring your own device" (BYOD) scenarios, where conventional perimeter-based security measures fall short.
Frameworks like SPIFFE allow services to have identities that are not tied to specific network locations, enabling fine-grained policies across on-premises setups and multi-cloud environments. For instance, the NIST National Cybersecurity Center of Excellence collaborated with 24 industry partners to create 19 real-world examples showcasing how PKI can be integrated into modern Zero Trust architectures.
Once identity verification is established, managing certificates at scale becomes the next critical step.
Using PKI-as-a-Service for Scalability
Managing certificates manually is not a viable solution for large-scale operations. Without a well-structured TLS program, expired or poorly managed certificates can lead to serious security vulnerabilities. Automating certificate lifecycle management is essential to avoid incidents that could disrupt business operations or compromise security.
PKI-as-a-Service simplifies this by automating processes like certificate discovery, issuance, renewal, and revocation across diverse environments. This is particularly important when managing thousands – or even millions – of identities across multiple cloud platforms. To support this automation, the infrastructure should include tools like API gateways and sidecar proxies that enforce authentication and authorization policies at the application level, regardless of where the services are hosted.
A robust certificate management program should incorporate best practices for large-scale server certificate management. This includes integrating PKI with Identity, Credential, and Access Management (ICAM) systems and Enhanced Identity Governance (EIG). These integrations ensure secure access to resources across both on-premises and cloud environments while maintaining consistent security policies.
Scalable hosting solutions, such as those offered by Serverion, provide the foundation needed for automated PKI deployments, supporting the broader goals of a Zero Trust strategy.
While automation addresses scalability, combining PKI with additional security layers further strengthens Zero Trust frameworks.
Combining PKI with MFA and SSO
PKI enhances Multi-Factor Authentication (MFA) by introducing a phishing-resistant, hardware-linked factor. Research shows that 96% of IT security executives view PKI as essential for building a Zero Trust architecture.
"PKI, in conjunction with MFA, is one of the more secure ways to implement Zero Trust." – Dr. Avesta Hojjati, DigiCert
This approach layers multiple security factors. For example, a smart card with a digital certificate (possession) can be combined with a PIN (knowledge) or biometrics (inherence) for stronger authentication. Single Sign-On (SSO) systems also leverage PKI to verify user identities across multiple cloud applications. This eliminates the need for managing multiple passwords while maintaining strong certificate-based verification. The result? A streamlined, secure user experience that resists phishing attempts and aligns with Zero Trust’s "never trust, always verify" principle.
Given that business email compromise accounted for $2.77 billion in reported losses in 2024, these protections are more important than ever. Best practices include using certificate-based authentication for VPN access, requiring MFA for sensitive PKI operations (like certificate issuance or revocation), and storing private keys in Hardware Security Modules (HSMs) to prevent unauthorized access or compromise. Despite these advancements, 33% of industry authentication tools still rely on OTP-based MFA, underscoring the need for broader adoption of PKI-backed solutions.
sbb-itb-59e1987
PKI Challenges and Best Practices for Zero Trust
Certificate Lifecycle Management
Managing TLS certificates can quickly spiral out of control, leading to what’s often called "certificate sprawl." This happens when certificates are scattered across an organization without a centralized inventory to track them. The result? Expired certificates that go unnoticed, causing outages and leaving security gaps wide open. Relying on manual processes to track certificate owners, renewal dates, and configurations simply doesn’t scale in today’s complex environments.
"Despite the critical importance of these certificates, many organizations lack a formal TLS certificate management program and do not have the ability to centrally monitor and manage their certificates." – Murugiah P. Souppaya et al., NIST
The fix? Automation. Protocols like ACME can take over tasks like enrollment, installation, and renewal, eliminating the need for constant human oversight. Tools for continuous monitoring can detect changes in certificate status, ensuring renewals happen on time and outages are avoided. To make this work, organizations need a formal TLS management program that sets clear policies and assigns ownership of certificates.
When these automated processes are paired with established standards, PKI becomes a stronger foundation for Zero Trust architecture.
Meeting Security Standards with PKI
To ensure security measures are consistent and effective, aligning PKI implementation with widely recognized frameworks is crucial. Standards like NIST SP 800-207 and ISO/IEC 27001 emphasize the importance of robust certificate lifecycle management. These frameworks also underline a key principle of Zero Trust: authentication and authorization must occur separately and before every session.
"Zero trust assumes there is no implicit trust granted to assets or user accounts based solely on their physical or network location… Authentication and authorization (both subject and device) are discrete functions performed before a session to an enterprise resource is established." – NIST SP 800-207
By mapping PKI capabilities to these standards, organizations can identify areas where they lack visibility, governance, or the ability to recover from incidents. A practical example of this approach comes from the NIST National Cybersecurity Center of Excellence, which demonstrated 19 Zero Trust implementations using technology contributions from 24 industry collaborators. These examples provide actionable models for organizations looking to strengthen their security posture.
Manual vs. Automated PKI Management
The case for automation becomes even clearer when comparing manual and automated PKI management. Here’s a breakdown of how they stack up in key areas:
| Feature | Manual PKI Management | Automated PKI Management |
|---|---|---|
| Efficiency | Low; prone to human error and delays. | High; automates enrollment, installation, and renewal. |
| Scalability | Challenging as networks grow. | Easily handles growth in devices and services. |
| Zero Trust Alignment | Weak; struggles to meet dynamic authentication demands. | Strong; supports rapid certificate rotation and continuous verification. |
| Risk of Outage | High; expired certificates often go unnoticed. | Low; automated tracking minimizes downtime. |
| Visibility | Fragmented and outdated. | Centralized and real-time. |
Automation doesn’t just reduce the risk of outages or human error – it also provides the agility needed for modern, hybrid workforces that operate across both on-premises and cloud environments. Additionally, automated tools make disaster recovery faster and more reliable when a Certificate Authority is compromised. In short, automation is a cornerstone of any effective Zero Trust strategy.
Conclusion
Public Key Infrastructure (PKI) plays a central role in making Zero Trust Architecture a reality. By tying digital identities to users, devices, and applications, PKI moves security away from outdated network boundaries and focuses on identity-based verification. This shift embodies the core Zero Trust principle: never trust, always verify. As cyber threats evolve, the demand for automated and streamlined PKI management continues to grow.
The numbers speak for themselves: 96% of IT security executives recognize PKI as a critical component of building a Zero Trust framework. It delivers authentication, encryption, and data integrity across both on-premises and cloud environments. With TLS certificate lifespans now averaging just 47 days, automating lifecycle management, maintaining centralized oversight, and enabling continuous monitoring are no longer optional – they are essential to avoid costly outages. Currently, 33% of organizations have implemented Zero Trust strategies, and another 60% aim to follow suit within the next year.
The push toward identity-based security is gaining momentum, fueled by the rise of remote work, the proliferation of IoT devices, and regulatory pressures such as U.S. Executive Orders mandating Zero Trust adoption for federal agencies. Organizations that align their PKI strategies with frameworks like NIST SP 800-207 and invest in automation will be better equipped to tackle today’s cyber risks and adapt to future challenges, including the shift to post-quantum cryptography.
FAQs
What role does PKI play in supporting Zero Trust Architecture?
Public Key Infrastructure (PKI) plays a crucial role in Zero Trust Architecture by providing the cryptographic backbone for its guiding principle: “never trust, always verify.” Through PKI, digital certificates are used to authenticate users, devices, and services, ensuring secure and tamper-resistant verification. This aligns perfectly with Zero Trust’s demand for thorough verification at every access point.
One key feature PKI enables is mutual TLS (mTLS). With mTLS, both the client and the server verify each other’s identities before any data is exchanged. This not only secures communication but also ties access permissions directly to authenticated identities, reinforcing the principle of least-privilege access.
PKI also ensures data protection through encryption. By leveraging SSL/TLS certificates, it encrypts communication channels, making them secure against threats like eavesdropping or man-in-the-middle attacks. Additionally, PKI supports dynamic security needs with automated certificate management. This allows for the immediate revocation of compromised certificates, ensuring that access control remains secure even in rapidly changing environments.
These capabilities make PKI an indispensable part of any strong Zero Trust security framework.
How does automation simplify PKI management in a Zero Trust model?
Automation plays a critical role in managing Public Key Infrastructure (PKI) within a Zero Trust framework. In this model, every user, device, and service must authenticate before exchanging data. This creates a need for issuing, renewing, and revoking thousands – or even tens of thousands – of certificates. Handling this volume manually is unrealistic. Automation steps in to ensure certificates are generated, distributed, and rotated efficiently, reducing the risk of human error while upholding the core principle of Zero Trust: "never trust, always verify."
For Serverion customers, automation simplifies SSL certificate and server management. It enables fast, programmatic enrollment of trusted identities for web traffic, APIs, and microservices. This creates a scalable, secure trust framework that aligns seamlessly with Zero Trust principles.
Why is TLS 1.3 the preferred choice for Zero Trust security frameworks?
TLS 1.3 stands out as the go-to choice in Zero Trust environments due to its improved security and efficiency over TLS 1.2. By incorporating mandatory forward secrecy, it ensures that even if encryption keys are exposed, previous communications stay protected.
On top of that, TLS 1.3 minimizes handshake latency, allowing for quicker connection setups without compromising encryption strength. This combination of robust security and faster performance makes it a perfect fit for the stringent demands of Zero Trust frameworks, where both high security and low latency are critical.







