Checklist for Key Management Compliance
Protecting your encryption keys is as important as encrypting your data. Without proper key management, even the strongest encryption becomes useless. This guide provides a step-by-step checklist to ensure your key management strategy aligns with frameworks like ISO 27001, PCI DSS, and NIST standards.
Key Takeaways:
- Key Generation: Use NIST-approved algorithms and validated cryptographic modules.
- Key Distribution: Securely transmit keys via key wrapping or key agreement methods.
- Key Storage: Store keys in FIPS 140-3 compliant HSMs; never leave keys in plaintext.
- Access Control: Enforce role-based access and multi-factor authentication (MFA).
- Key Rotation: Automate rotations to limit risk while minimizing disruptions.
- Key Revocation & Destruction: Automate revocation and securely erase outdated keys.
- Monitoring & Auditing: Log every key-related activity and conduct regular audits.
Key Deadlines:
- Transition to FIPS 140-3 compliant modules by September 22, 2026.
By following this checklist, you can safeguard sensitive data, streamline compliance, and reduce risks associated with encryption key mismanagement. Let’s dive deeper into each step.
8 Cryptographic Key Management Best Practices
Key Generation and Distribution Checklist
Strong key generation and secure distribution are essential for meeting the compliance mandates discussed earlier.
Use Cryptographically Strong Random Number Generators
Keys must be created using NIST-approved algorithms within validated cryptographic modules. The random bit generator (RBG) you choose should provide security strength equal to or greater than the key being generated. Any weaknesses in randomness can expose your system to prediction attacks.
Refer to NIST SP 800-133 for guidance on key generation and ensure the use of FIPS-validated modules. As stated in NIST SP 800-133 Rev. 2:
"Cryptography relies upon two basic components: an algorithm (or cryptographic methodology) and a cryptographic key."
Document these processes in your Key Management Practice Statement (KMPS) to demonstrate compliance during audits. Additionally, stay updated with NIST SP 800-131A to monitor changes in algorithm strength and key length requirements as standards evolve.
Once you’ve established secure key generation, the next step is ensuring safe key distribution.
Ensure Secure Key Distribution Methods
After keys are generated, they must be distributed securely to their intended destination. Two primary methods are commonly used:
- Key Transport: One party generates the key, encrypts it, and sends it to the other party.
- Key Agreement: Both parties contribute to the creation of a shared secret, such as during a Diffie-Hellman exchange.
To protect keys during transmission over untrusted channels, use key wrapping – encrypting a symmetric key with another key. Always rely on validated cryptographic modules for both key generation and distribution, and automate these processes to minimize human error.
Log every key distribution event, including participant identities and timestamps, to maintain a clear audit trail. Implement key derivation functions to generate multiple sub-keys from a single secure exchange, reducing the need for frequent full key distributions.
Once keys are securely transmitted, ensure your infrastructure can handle the computational demands of these cryptographic operations.
Ensure Adequate Computational Resources
Key generation and distribution require significant processing power. Hardware Security Modules (HSMs) are dedicated devices designed to handle these cryptographic tasks, relieving your primary servers of the load. Cloud-based HSMs provide a scalable alternative, offering key management as a service without the need for upfront hardware investments.
Align your infrastructure with your operational needs. As noted in NIST SP 800-57 Part 2:
"Planning and documentation requirements associated with small scale or single system cryptographic applications will not need to be as elaborate as those required for large and diverse government agencies."
To enhance security, use quorum controls within HSMs. These controls require multiple authorized individuals to approve critical changes, reducing the risk of single points of failure while maintaining a manageable workflow for your team.
Key Storage and Access Control Checklist
Once you’ve nailed down secure key generation and distribution, the next step is critical: protecting those keys from unauthorized access. Without proper safeguards, even the best encryption won’t keep your data secure.
Use Hardware Security Modules (HSMs) or Encrypted Storage
When it comes to key protection, Hardware Security Modules (HSMs) are the gold standard. These tamper-resistant devices ensure keys are isolated and prevent plaintext export. If you’re working toward compliance, make sure your HSMs meet FIPS 140-2 Level 3 or the updated FIPS 140-3 standard. Keep in mind, organizations must move to FIPS 140-3-compliant modules by September 22, 2026, as certifications for FIPS 140-2 will no longer be valid for new deployments after that date.
Keys should never be directly accessible to users. Ensure they are encrypted at rest and only processed within secure cryptographic modules. A great way to add an extra layer of security is through envelope encryption: encrypt your data with a data key, then encrypt that data key with a root key stored in an HSM or key management service. This means even if someone gets hold of encrypted data, they can’t decrypt it without accessing the root key, which is securely protected.
Cloud-based HSMs offer a scalable and cost-effective option. Depending on your organization’s needs, you can choose between distributed keys (stored alongside workloads) or centralized keys (managed in a dedicated security account). Your decision should align with your compliance goals and operational structure.
Once your keys are securely stored, the next priority is controlling who can access them.
Implement Role-Based Access Controls (RBAC) and Multi-Factor Authentication (MFA)
Access control should always start with the Principle of Least Authority – users should only have the permissions they need, and nothing more. Separate responsibilities between administrators managing keys and applications using them. This segregation of duties ensures no single individual has full control over the cryptographic process.
For sensitive tasks, like changing key policies or deleting keys, consider using quorum schemes (also known as m-of-n controls). These require a minimum number of authorized individuals to approve an action, reducing the risk of accidental or malicious key loss while maintaining flexibility.
Multi-Factor Authentication (MFA) is essential for securing critical access points, especially for root access keys. The Centers for Medicare & Medicaid Services (CMS) advises against using root access keys altogether or, at the very least, protecting them with MFA. Weak access controls are a direct contributor to costly data breaches.
Leverage automated tools like IAM Access Analyzer to catch overly permissive key policies before they cause problems. Set up alerts via security hubs or Cloud Security Posture Management (CSPM) tools to flag misconfigurations or keys scheduled for deletion. Most key management services include a mandatory waiting period – usually 30 days – before keys are permanently deleted, giving you time to catch and correct mistakes.
Once you’ve crafted strong access policies, focus on restricting and monitoring personnel access to ensure key integrity.
Restrict Access to Authorized Personnel
Even with secure storage and access controls in place, it’s vital to monitor and limit key usage to authorized personnel.
Accountability is the cornerstone of effective access control. Every key access should be logged with details such as user, time, and action. This audit trail not only helps identify potential compromises but also discourages misuse and aids in recovery by pinpointing which data a compromised key protected.
Regularly review access logs and permissions. Consider segregating key management logs into a separate trail to reduce volume and improve security monitoring. Always verify that access aligns with current job roles – people change positions, and their permissions should reflect those changes.
Keys should never be stored in plaintext or directly accessed by applications. Instead, they should only be processed within secure cryptographic modules or vaults. When sharing keys is unavoidable, use secure, out-of-band methods – never send a key alongside the data it protects.
Key Usage and Rotation Checklist
While secure storage is crucial, it’s only part of the equation. Proper usage and regular rotation of cryptographic keys are essential for maintaining compliance and protecting sensitive data. Let’s break it down.
Monitor and Log Key Usage
Keeping a detailed record of every cryptographic operation – whether it’s encryption, decryption, or even a read-only API call – is critical for maintaining an effective audit trail. According to NIST SP 800-57, “Audit and Accountability” is a core element of cryptographic key management. These records ensure the integrity of the key lifecycle and help you stay on top of security.
Real-time monitoring is equally important. Tools like CSPM can send alerts for unusual activity, such as a sudden spike in decryption requests from an unfamiliar IP address or service accounts accessing keys at odd hours. These could be red flags for credential misuse or compromise. Configuring alerts for suspicious behavior or misconfigurations can help you act quickly and prevent potential breaches.
Regularly reviewing logs is a must, especially during compliance audits or investigations. Pay close attention to high-risk events like key destruction or deletion requests. Most key management systems enforce a waiting period – typically 30 days, with a minimum of 7 days – before permanently deleting keys. This buffer allows you to reverse unauthorized actions if needed.
Once logging and monitoring are in place, the next step is ensuring keys are rotated regularly to maintain security and compliance.
Establish Key Rotation Schedules
Rotating keys on a regular schedule limits their exposure and reduces the risk of compromise. Automated key rotation is the gold standard here – it minimizes human interaction with sensitive key material and eliminates the risk of manual errors.
Set rotation schedules based on the lifespan of each key. Many regulations, including GDPR, CCPA, and PCI DSS, require robust key management practices, with rotation being a key component for compliance.
"If one does not protect the encryption keys, there is no point in encrypting the data – find the keys, access the data." – Entrust
Automated tools make enforcing rotation policies seamless. Regularly audit these policies and review IAM permissions to ensure only authorized users have access, adhering to the principle of least privilege. For environments with heightened security needs, consider implementing quorum controls through Hardware Security Modules (HSMs). This ensures that no single individual can alter key rotation policies without oversight.
Minimize Operational Disruption During Rotations
Key rotations don’t have to disrupt your operations. Envelope encryption is a smart approach – it allows you to rotate a master key without re-encrypting your entire dataset. The old key transitions to a "post-operational" state, where it can still decrypt existing data, while the new key takes over all new encryption tasks. Managed services handle these updates seamlessly, ensuring your applications continue to function without interruption.
"Using a software solution will provide more reliable management of keys than performing the steps manually." – CMS Key Management Handbook
To reduce risks during rotations, use standardized key management libraries for compatibility and reliability. Always back up your keys securely before initiating a rotation to avoid accidental data loss. Define clear cryptoperiods – the time frame during which a key is valid – and schedule rotations during periods of low activity. This minimizes disruptions and keeps your operations aligned with security protocols.
sbb-itb-59e1987
Key Revocation and Destruction Checklist
When a key becomes compromised or outdated, acting quickly to revoke and destroy it is critical. The difference between containing an incident and facing a full-blown breach often hinges on how swiftly and effectively you handle this process.
Automate Revocation Lists and Updates
Speed is everything when it comes to revoking compromised keys. Relying on manual processes leaves dangerous gaps that attackers can exploit before your systems catch up. Automated tools like Certificate Revocation Lists (CRLs) or the Online Certificate Status Protocol (OCSP) help ensure revocation updates are distributed across your network in real time, shrinking the window of vulnerability. Configure your key management system to immediately flag compromised keys, halting their ability to protect new data while you address the issue.
Role-based access controls (RBAC) are essential here – only authorized personnel should have the ability to initiate key revocations. This prevents accidental disruptions or malicious actions. Centralized logging tools, such as AWS CloudTrail, can help you monitor for unusual activity or unauthorized revocation attempts, providing a clear audit trail.
Once revocation is automated, focus on secure backup and destruction procedures.
Secure Key Backups and Destruction
Deleting a key isn’t as simple as pressing a button. Every copy of the key, including backups and archives, must be securely erased. According to NIST SP 800-57 Part 2, organizations must establish a Key Management Policy (KMP) and a Key Management Practice Statement (KMPS) that clearly outline destruction procedures.
"Establish and manage cryptographic keys when cryptography is employed within the system in accordance with the following key management requirements: [Assignment: organization-defined requirements for key generation, distribution, storage, access, and destruction]." – NIST SP 800-53
For secure destruction, use FIPS 140-2/3 validated Hardware Security Modules (HSMs) to ensure key material is rendered completely unrecoverable. Synchronize backup and destruction processes to eliminate any leftover key material that could be exploited.
Establish cryptoperiods – specific timeframes during which a key remains valid – for every key type. Automating the identification of obsolete keys ensures they’re retired securely and on schedule. When moving away from older algorithms or shorter key lengths, follow NIST SP 800-131A guidelines to safely retire outdated material without leaving security gaps.
Responding to Compromised Keys
When a key is compromised, quick action is vital. Incident response protocols should kick in immediately, starting with an investigation into how the breach occurred. Assess any data encrypted with the compromised key and verify your key inventory to identify all affected instances.
After revoking the key, conduct a compliance audit to ensure that all systems have updated their key stores and that your incident response plan was executed properly. These reviews can expose weak points in your procedures and help you strengthen them for the future.
For organizations relying on cloud services or external data centers, maintaining physical control over cryptographic keys is critical. Being able to destroy keys – either physically or logically – without depending solely on the provider’s processes ensures your data remains secure, even if the provider’s systems are compromised. These measures complete the key management lifecycle and align with broader security and compliance standards.
Monitoring, Auditing, and Documentation Checklist
Keeping track of key activities and documenting every step helps ensure compliance and identify potential issues early. This process forms the backbone for thorough audits, accurate logging, and effective staff training.
Conduct Regular Audits and Continuous Monitoring
Once you’ve established secure key storage and controlled usage, the next step is regular audits and ongoing monitoring to maintain a strong lifecycle policy. Tools like Cloud Security Posture Management (CSPM) can help detect misconfigurations and unusual activities. CSPM tools automatically flag issues such as misconfigured key policies, keys scheduled for deletion, or keys missing automated rotation. Automated analyzers can periodically review key policies and alert administrators to overly broad permissions that go against the principle of least privilege.
"It is best practice to monitor the use of encryption keys to detect unusual access patterns." – AWS Well-Architected Framework
Auditing your trust stores is equally important. Ensure they only contain approved certificates and trust anchors. Confirm that all cryptographic modules meet standards like FIPS 140-2 Level 3, and remember that CMS information systems must transition to FIPS 140-3-compliant modules by September 22, 2026.
Maintain Logs and Audit Trails
Automated logging is essential for capturing every API call and operation, providing a complete accountability trail. For high-volume environments, consider separating key management logs into a dedicated audit trail to make them easier to review and manage.
Special attention should be given to high-risk events, such as key destruction. For instance, AWS KMS enforces a default 30-day waiting period before permanently deleting key material. This gives administrators time to review and potentially reverse any unauthorized deletion requests. Monitoring these events closely can help detect malicious activity during the waiting period.
Your logs should detail who accessed keys, when, and for what purpose. This level of transparency discourages improper use and supports incident investigations. Use IAM and key policies to enforce least privilege, and regularly review logs to identify unusual access patterns that could indicate a security issue. These detailed logs are also valuable for training programs, as they highlight the importance of accountability and proactive monitoring.
Provide Training on Key Management Practices
Documentation alone isn’t enough – your team needs to understand and follow the procedures. Create and update training materials that clearly explain your key management practices and roles. Define responsibilities for each function and actively communicate approved policies to all relevant staff.
Policies and procedures should be reviewed and updated at least once a year to address new technologies and evolving threats. For CMS information systems, risk assessments must be reviewed at least every three years – or sooner if there are major system changes. Modern documentation should also include an inventory of cryptographic dependencies to pinpoint systems vulnerable to quantum threats and outline a plan for transitioning to post-quantum cryptography.
Compliance Standards Comparison Table
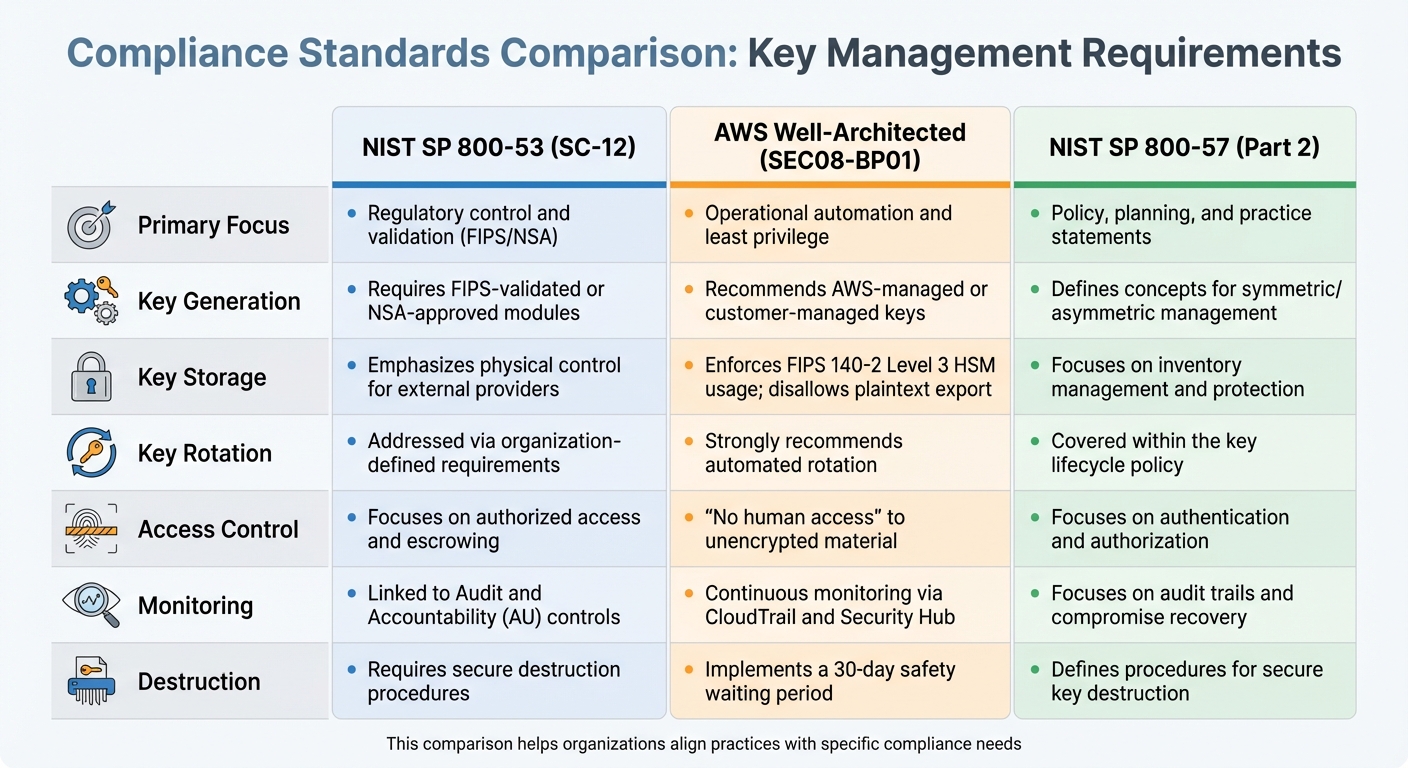
Key Management Compliance Standards Comparison: NIST SP 800-53 vs AWS Well-Architected vs NIST SP 800-57
Compliance frameworks differ in their approach to key management, each emphasizing unique aspects. NIST SP 800-53 prioritizes regulatory control and validation, mandating FIPS-validated or NSA-approved technology for key generation. AWS Well-Architected Framework focuses on operational automation and ensuring that key material is never accessible to human identities in plain text. Meanwhile, NIST SP 800-57 offers a broader perspective, outlining policy and planning guidance through its multi-part framework.
Here’s a side-by-side comparison of these standards across key categories:
| Category | NIST SP 800-53 (SC-12) | AWS Well-Architected (SEC08-BP01) | NIST SP 800-57 (Part 2) |
|---|---|---|---|
| Primary Focus | Regulatory control and validation (FIPS/NSA) | Operational automation and least privilege | Policy, planning, and practice statements |
| Key Generation | Requires FIPS-validated or NSA-approved modules | Recommends AWS-managed or customer-managed keys | Defines concepts for symmetric/asymmetric management |
| Key Storage | Emphasizes physical control for external providers | Enforces FIPS 140-2 Level 3 HSM usage; disallows plaintext export | Focuses on inventory management and protection |
| Key Rotation | Addressed via organization-defined requirements | Strongly recommends automated rotation | Covered within the key lifecycle policy |
| Access Control | Focuses on authorized access and escrowing | "No human access" to unencrypted material | Focuses on authentication and authorization |
| Monitoring | Linked to Audit and Accountability (AU) controls | Continuous monitoring via CloudTrail and Security Hub | Focuses on audit trails and compromise recovery |
| Destruction | Requires secure destruction procedures | Implements a 30-day safety waiting period | Defines procedures for secure key destruction |
This table highlights where each framework places its emphasis, making it easier to align practices with specific compliance needs. For organizations seeking to streamline their approach, NIST SP 800-57 can serve as a unified framework to map common regulatory elements, helping to reduce management complexity. For detailed instructions on meeting these standards, refer to the relevant sections in the compliance checklist.
Conclusion
Managing cryptographic keys effectively is the backbone of any secure encryption system. As highlighted in the CMS Key Management Handbook, "The security of the cryptosystem is dependent upon successful key management." Even the most advanced encryption becomes meaningless if keys are mishandled, leaving sensitive data vulnerable to unauthorized access.
To help protect encrypted data and meet regulatory standards, following a clear set of best practices is essential. By implementing the steps outlined in the checklist, you establish multiple layers of protection against both external attacks and internal mistakes. As OWASP warns, even the most secure systems can fail due to human errors, making documented procedures and accountability critical components of your strategy.
It’s also worth noting that losing encryption keys renders data permanently inaccessible. Beyond security, proper key management supports operational continuity and ensures compliance with federal regulations. For instance, the September 22, 2026 deadline for CMS systems to adopt FIPS 140-3-compliant modules is fast approaching, underscoring the urgency to refine your key management processes.
Now is the time to assess your current practices using the checklist, identify any weak points, and prioritize secure, automated solutions. Investing in strong key management today not only helps prevent breaches and data loss but also ensures you stay ahead of regulatory requirements.
FAQs
What happens if organizations don’t switch to FIPS 140-3 compliant modules by 2026?
Failing to switch to FIPS 140-3 compliant modules by 2026 brings serious risks. Organizations could face non-compliance with federal regulations, which might strip them of certifications essential for specific operations. On top of that, relying on outdated encryption standards heightens the risk of security vulnerabilities and cryptographic breaches, leaving sensitive data exposed.
To steer clear of these challenges, it’s crucial to upgrade all encryption key management systems to align with FIPS 140-3 requirements well ahead of the deadline.
What are the best practices for securely distributing encryption keys over untrusted networks?
To safely share encryption keys across networks that might not be secure, it’s crucial to rely on strong cryptographic techniques. For instance, encryption can shield keys during transmission, while secure protocols like TLS ensure that data stays private and protected from interception. Adding strict access controls and authentication measures further strengthens security by verifying the identities of those involved in the key exchange. This approach helps minimize threats like unauthorized access or man-in-the-middle attacks.
Protocols like Diffie-Hellman and Public Key Infrastructure (PKI) are also excellent tools for secure key exchanges. These methods rely on digital certificates and secure processes to establish and share keys without exposing sensitive data. By combining encryption, secure protocols, and strong authentication, organizations can confidently handle key distribution, even in less trustworthy network environments.
Why is automating key rotation and revocation important for security and compliance?
Automating key rotation and revocation plays a crucial role in safeguarding sensitive data and adhering to security standards. Relying on manual methods can be time-consuming, error-prone, and may leave gaps that attackers can exploit.
With automation, encryption keys can be updated promptly, minimizing the risk of breaches and ensuring compliance with regulations. It also eases the burden on IT teams, freeing them up to address other pressing security needs.







