Securing APIs: Encrypting Sensitive Data End-to-End
APIs drive modern technology, but without proper encryption, they expose sensitive data to serious risks. From stolen passwords to compliance violations, unsecured APIs can lead to breaches, fines, and reputational damage. Here’s what you need to know to protect your APIs effectively:
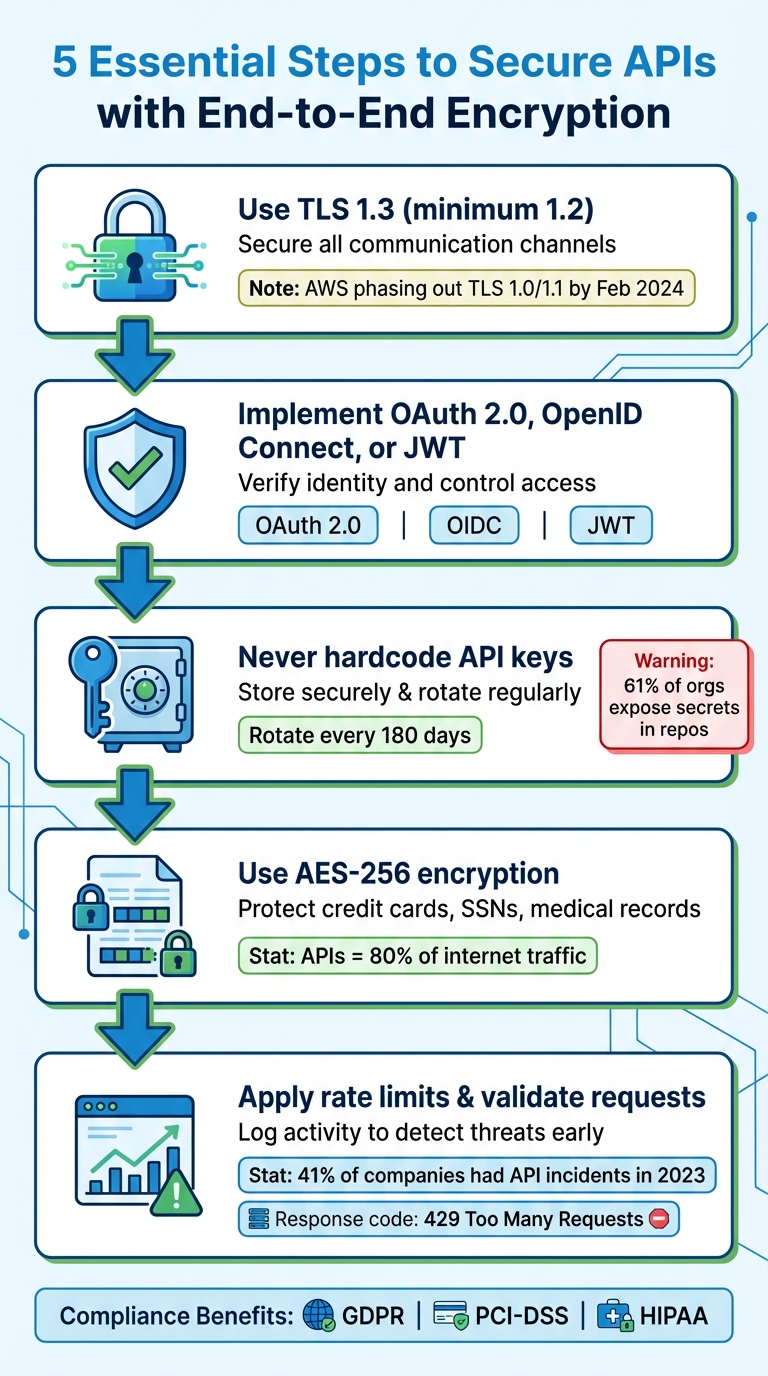
- Encrypt All Data in Transit: Use TLS 1.3 (or at least 1.2) to secure communication channels.
- Authenticate and Authorize Safely: Implement OAuth 2.0, OpenID Connect, or JWT for secure access control.
- Handle Credentials Carefully: Avoid hardcoding API keys; store them securely and rotate them regularly.
- Secure Sensitive Fields: Use AES-256 encryption for critical data like credit card numbers or personal details.
- Monitor and Limit Usage: Apply rate limits, validate requests, and log activity to detect threats early.
These steps not only protect your data but also help meet regulations like GDPR, PCI-DSS, and HIPAA. Keep reading for detailed guidance on how to implement these practices and secure your APIs from end to end.
5 Essential Steps to Secure APIs with End-to-End Encryption
API Security: How to Protect Your APIs (Best Practices) | API Security Tutorial #api
Basic Security Requirements for APIs
Strong authentication and careful credential management form the foundation of secure API encryption.
Authentication and Authorization Methods
Authentication confirms who is making an API request, while authorization determines what actions that user or system is allowed to perform. As the NCSC explains:
Authentication verifies the identity of the entity making an API request, while authorisation controls what actions the authenticated entity is allowed to perform.
One of the most widely used standards for delegated access is OAuth 2.0, enabling third-party apps to access resources without exposing passwords. For cases where verifying a user’s identity is also necessary, OpenID Connect (OIDC) builds on OAuth 2.0 by adding an identity layer, issuing ID tokens for authentication. Meanwhile, JSON Web Tokens (JWT) are often used as stateless tokens that securely carry information (claims) between parties. These tokens consist of three parts: a header, a payload, and a signature.
The best choice of authentication method depends on your specific needs. API keys are straightforward for basic service-to-service communication but lack critical features like expiration and are vulnerable if leaked. For mobile apps or single-page applications, JWT bearer tokens offer stronger security. For scenarios involving user logins or third-party integrations, OAuth 2.0 with OIDC provides the most comprehensive protection.
Authorization can be managed through patterns like Role-Based Access Control (RBAC), which assigns permissions based on predefined roles, or Attribute-Based Access Control (ABAC), which uses attributes of users and resources for more detailed control. Regardless of the approach, stick to three key principles: grant least privilege access, deny by default unless explicitly allowed, and validate permissions on every request instead of relying on one-time checks.
These practices create a solid foundation for encrypting API communications.
Managing API Keys and Credentials Securely
Even the strongest authentication can be undermined by poor credential management. Hardcoding API keys or committing them to version control is especially dangerous, as attackers often scan public repositories for exposed credentials. Google Cloud underscores this risk:
API keys are bearer credentials. This means that if someone steals an API key… they can use it to authenticate… and access the same resources.
To prevent such vulnerabilities, store credentials securely in environment variables on the server side or use specialized tools like AWS Secrets Manager or HashiCorp Vault to avoid "secrets sprawl." Always transmit credentials over secure HTTP headers, and for web applications, use httpOnly and Secure cookies to protect tokens from cross-site scripting (XSS) attacks.
Automating API key rotation reduces the risk of misuse. Assign unique API keys to each application or user to simplify auditing and minimize the impact of a leak. Add restrictions to API keys, such as limiting their use to specific IP addresses, HTTP referrers, or API endpoints. The NCSC advises:
The lifetime of a credential should be only set to the appropriate amount of time appropriate to the use case and threat.
For production systems handling sensitive data, consider transitioning from simple API keys to more secure methods like OAuth 2.0 or signed JWTs. Additionally, enforce rate limits using API keys to control usage and protect against denial-of-service attacks. When limits are exceeded, return a 429 Too Many Requests status code.
How to Encrypt API Communications
Securing data during its journey between clients and servers requires multiple layers of protection. While transport-level encryption secures the communication channel, field-level encryption adds an extra layer of security for specific sensitive data.
Setting Up HTTPS and TLS for APIs
To ensure secure data transmission, every API should operate using TLS version 1.2 or higher. For optimal security and performance, TLS 1.3 is the recommended choice. Obtain SSL/TLS certificates from trusted Certificate Authorities like Let’s Encrypt or GlobalSign. Avoid self-signed certificates, as they often trigger security warnings.
If you’re using NGINX, configure your server to listen on port 443, specify the paths for ssl_certificate and ssl_certificate_key, and redirect HTTP traffic on port 80 to HTTPS using a 301 redirect. For Apache, enable the mod_ssl module, include the SSLEngine on directive, and define your certificate files within a <VirtualHost *:443> block. Use strong cipher suites such as TLS_AES_128_GCM_SHA256 or TLS_CHACHA20_POLY1305_SHA256, and disable outdated ciphers like RC4, MD5, and 1024-bit RSA keys.
To further enhance security, implement the HTTP Strict Transport Security (HSTS) header with a max-age of at least six months (15,768,000 seconds). This ensures clients exclusively use HTTPS, preventing downgrade attacks that attempt to revert connections to unencrypted HTTP. For scenarios requiring high security, such as B2B integrations or IoT devices, consider mutual TLS (mTLS), which mandates both server and client to authenticate with valid X.509 certificates.
It’s worth noting that AWS plans to phase out TLS 1.0 and 1.1 by February 2024, emphasizing the need to upgrade to modern protocols.
Encrypting Specific Data Fields
While TLS secures the communication channel, field-level encryption protects highly sensitive information within API payloads, such as Social Security numbers, credit card details, or medical records. Encrypt these fields individually, using AES-256, before transmission.
To ensure both confidentiality and integrity, use authenticated encryption methods. This prevents attackers from tampering with the encrypted data, even if they cannot decrypt it. In cases where channel encryption terminates at untrusted proxies or shared hardware, apply message-level encryption with tools like the AWS Encryption SDK to keep data secure throughout its entire journey.
API-related data breaches are on the rise, with APIs now accounting for over 80% of internet traffic. Alarmingly, API-related breaches have increased by 80% year over year. A stark example: a single compromised API key enabled a major breach of the US Department of the Treasury by Chinese hackers in December 2024. These incidents underscore the importance of encrypting sensitive fields, even when TLS is in use.
Additionally, sanitize sensitive fields in API logs. Mask or redact values to prevent accidental exposure in monitoring systems or log files.
Managing Encryption Keys
Encryption is only as strong as the keys protecting it, so effective key management is a must. Use dedicated services like AWS Key Management Service (KMS), Azure Key Vault, or Google Cloud KMS to store cryptographic keys securely. These services offer centralized repositories with built-in security controls and high availability.
Limit access to encryption keys with Role-Based Access Control (RBAC) or IAM policies, granting only the permissions necessary for specific roles. Implement machine-to-machine authentication and automate processes wherever possible. To further secure access, configure firewalls to allow requests only from trusted IP ranges or virtual networks, and use private endpoints to keep traffic off the public internet.
Rotate API keys and secrets at least every 180 days using automated tools. This minimizes the risk posed by compromised keys. Use an encryption context, a set of non-secret key-value pairs that must match during both encryption and decryption, to bind keys to specific resources. For example, AWS KMS can use the API Gateway ARN as part of the encryption context.
Monitor all key access attempts with tools like AWS CloudTrail or Azure Monitor. Set up alerts for unauthorized or suspicious activity to detect potential breaches early. Finally, automate certificate renewal to avoid service disruptions caused by expired credentials.
sbb-itb-59e1987
Additional Security Measures for APIs
APIs require multiple layers of defense to guard against threats beyond encrypted channels. These include attacks like injection attempts, credential stuffing, and resource exhaustion. The following measures build on encryption and credential protections to strengthen your API’s security posture. A strong, unique, and high-entropy password (or API key/secret) is still the foundation of credential security. Weak or reused credentials remain one of the most common entry points for credential stuffing, brute-force, and account takeover attacks — even when all other layers are properly implemented.
Validating Input and Encoding Output
Treat every incoming request as potentially harmful until proven otherwise. Start with schema validation, which ensures requests conform to predefined formats in JSON or XML. Reject anything that strays from these strict definitions. Use strong typing to enforce data integrity – integers for numbers, booleans for true/false values, and proper date formats for timestamps instead of generic strings.
Set clear constraints for each field. For example, limit string lengths, define acceptable numerical ranges, and use regular expressions to validate patterns. Always verify that the Content-Type header matches the actual payload, rejecting mismatches with a 415 Unsupported Media Type response. Similarly, enforce maximum request sizes to block oversized payloads, returning a 413 Payload Too Large if necessary.
"Having a well-defined request schema and validating against that schema should be the first line of defense against malicious messages." – Canada.ca
On the output side, ensure responses include explicit Content-Type headers like application/json to avoid misinterpretation. Add security headers such as X-Content-Type-Options: nosniff to prevent browsers from guessing file types incorrectly. Generic error messages are a must – don’t reveal internal details in responses. Additionally, sanitize logs to eliminate sensitive data or malicious code that could be exploited.
Pair these validation techniques with detailed logging to track unusual behavior effectively.
Tracking and Logging API Activity
Detailed logging is essential for identifying and responding to threats. Logs should capture key metadata, including the requester’s IP address, the accessed endpoint, the authenticated user or role, and timestamps for every interaction. This data becomes invaluable during investigations and helps pinpoint misuse when credentials are compromised.
Modern monitoring tools can provide real-time anomaly detection, flagging suspicious activity like sudden spikes in requests or unusual HTTP methods that might indicate automated abuse. Set up alerts for specific metrics, such as a surge in 401 Unauthorized errors, which could signal brute-force attacks or compromised credentials.
Unique API keys, as discussed earlier, are critical for tracking individual actions. Shared keys obscure accountability and make it harder to trace specific activities. Regularly rotate credentials and maintain an up-to-date inventory of all API endpoints, including deprecated ones that attackers might target. Combine these measures with strict usage controls to further secure your API.
Implementing Rate Limits
Rate limiting is a crucial defense against Denial of Service (DoS) attacks, credential stuffing, and excessive resource consumption by automated scripts. In 2023, 41% of companies reported experiencing API security incidents, with nearly one-third of all internet traffic attributed to malicious bots.
Set rate limits based on user authentication levels. For instance, anonymous users might be allowed 10 requests per minute, while registered users could have 100, and premium customers up to 1,000. If a client exceeds their limit, return a 429 Too Many Requests status code along with informative headers like X-RateLimit-Limit (total allowed), X-RateLimit-Remaining (remaining calls), and X-RateLimit-Reset (time until the limit resets).
To counter more sophisticated attackers, go beyond simple IP-based rate limiting. Use behavioral analysis to detect patterns, such as attackers rotating IP addresses. Shopify, for example, reduced credential stuffing attacks by 82% by implementing adaptive rate limiting that analyzed request behaviors. Combine these measures with monitoring to identify abuse patterns, such as multiple failed login attempts followed by a successful one – often a red flag for compromised credentials.
Practical Implementation Guidelines
Bringing security concepts into action requires careful planning and a solid grasp of potential pitfalls. Below are some practical tips to help you tackle real-world challenges and establish a secure, compliant API infrastructure.
Mistakes to Avoid
Even with strong encryption techniques, certain missteps can weaken your API security.
First, don’t rely on outdated protocols. Disable SSL v2, SSL v3, TLS 1.0, and TLS 1.1, as they’re riddled with vulnerabilities. Instead, configure your servers to use robust cipher suites like AES-GCM or ChaCha20-Poly1305, rejecting weaker options outright.
Another common error is using query parameters to pass API keys. Always send API keys through secure HTTP headers. A notable breach at a government agency occurred because API keys were exposed in query parameters, underscoring the importance of this practice.
Hardcoding credentials into source code or pushing them to repositories is a major risk – studies show that 61% of organizations have accidentally exposed secrets like API keys in public repositories. Instead, store credentials in environment variables or secure secret managers. When working with JWTs, never allow unsecured tokens (e.g., setting the algorithm to none) and always validate claims such as issuer, audience, and expiration. Additionally, store sensitive tokens in SameSite=Strict cookies rather than browser local storage, which is vulnerable to cross-site scripting attacks.
Compliance with Data Protection Regulations
Technical safeguards are only part of the equation – compliance with data protection laws is equally critical.
Encryption isn’t just a best practice; it’s often legally mandated. For instance, PCI-DSS v4.0 requires strong cryptography to protect cardholder data in transit, specifying TLS 1.2 or higher with secure cipher suites. Similarly, GDPR emphasizes encryption as a key measure for safeguarding personal data. In healthcare, HIPAA mandates encryption of electronic protected health information (ePHI) both at rest and in transit.
To meet these requirements, implement TLS 1.3, rotate certificates every 90 days, and use mutual TLS in high-security environments. Securely store keys using HSMs or managed Key Management Services to comply with SOC 2 standards. Finally, document your encryption practices, certificate rotations, and key management processes to ensure you can demonstrate compliance during audits.
Using Hosting Infrastructure for API Security
Modern hosting platforms come equipped with tools that enhance API security.
For example, DDoS mitigation at the infrastructure level can block common network and transport-layer attacks before they even reach your servers. Web Application Firewalls (WAFs) inspect HTTP traffic to filter out threats like SQL injection and cross-site scripting, stopping malicious payloads at the edge.
Some providers, like Serverion, offer infrastructure tailored for secure API deployments. Features include integrated SSL certificate management, automated certificate rotation, and DDoS protection across global data centers. Their dedicated servers and VPS options provide the network isolation needed to keep API traffic within private networks, minimizing exposure to public internet threats. For applications requiring mutual TLS – such as those in finance or healthcare – Serverion supports bi-directional authentication.
Virtual Private Clouds (VPCs) and private endpoints offer additional layers of security by isolating API traffic from the public internet. This is particularly useful for internal APIs that should remain inaccessible externally. Managed certificate services further simplify security by automating the issuance, deployment, and 90-day rotation of SSL/TLS certificates, reducing the risk of outages caused by expired certificates. These infrastructure tools work hand-in-hand with encryption and key management practices to provide comprehensive protection for your APIs.
Conclusion: Protecting Sensitive API Data
Implementation Steps Summary
To secure your APIs effectively, start by enforcing TLS 1.3 to encrypt all data in transit, including headers and query parameters. Move sensitive credentials from query strings to secure HTTP headers for added protection.
For industries like finance and healthcare, where security is paramount, consider implementing mutual TLS (mTLS) for two-way authentication between clients and servers. Pair this with token-based authentication methods like JWT or OAuth 2.0 in the Authorization header. For sensitive information, apply field-level encryption and use HMAC signatures to ensure request integrity.
Add another layer of defense with tools like Web Application Firewalls (WAFs), rate limiting, and centralized key management through HSMs or managed KMS solutions. Rotate certificates every 90 days and maintain detailed audit logs to align with compliance standards such as PCI DSS, GDPR, and HIPAA. These measures collectively form a robust, end-to-end API security framework.
Long-Term Benefits of API Security
Taking these steps doesn’t just address immediate vulnerabilities – it creates lasting value for your organization.
Strong API security prevents breaches, protects intellectual property, and safeguards personal data, all while building trust with users and partners. With APIs now handling 83% of all web traffic in 2023, robust encryption is no longer optional. Security incidents from the same year revealed that 42% involved data interception, 33% stemmed from credential leakage, and 25% resulted from Man-in-the-Middle attacks – issues that can be mitigated with proper encryption and layered defenses.
Encryption also makes compliance easier by reducing the scope of regulatory audits, saving both time and money. Companies that prioritize API security avoid the financial and reputational fallout of breaches like the 2023 T-Mobile API incident, which exposed 37 million records. By investing in encryption, regular key rotation, and infrastructure-level protections, organizations can create a scalable security foundation that adapts to evolving threats. Partnering with secure hosting providers, such as Serverion, can further enhance these protections while ensuring reliable performance and operational efficiency.
FAQs
What is the difference between OAuth 2.0 and OpenID Connect when it comes to API security?
OAuth 2.0 and OpenID Connect (OIDC) play distinct yet complementary roles in securing APIs.
OAuth 2.0 is all about authorization. It enables applications to access user resources on another service without needing to share login credentials. Instead, it uses access tokens to grant specific permissions, like reading data or performing certain actions.
OpenID Connect (OIDC) takes things a step further by adding an identity layer on top of OAuth 2.0. While OAuth 2.0 focuses on what an application is allowed to do, OIDC verifies who the user is through ID tokens. This makes it perfect for use cases like logging users in or confirming their identity.
To sum it up, OAuth 2.0 deals with permissions, while OpenID Connect ensures user authentication. Together, they provide a robust framework for secure and seamless interactions.
What is field-level encryption, and how does it improve API security beyond TLS?
Field-level encryption adds an extra layer of protection by encrypting specific sensitive data fields within an API. While TLS secures data during transmission, field-level encryption goes further by keeping sensitive information encrypted throughout its entire lifecycle – whether it’s being stored or processed.
With this method, only authorized systems or applications equipped with the right decryption credentials can access the protected data. By focusing on encrypting critical fields, this approach reduces the risk of data breaches or unauthorized access, even if other parts of the system are compromised.
Why is it important to regularly update and rotate API keys and encryption keys?
Keeping your API keys and encryption keys updated and rotated on a regular basis is a critical step in ensuring robust security. This approach limits the lifespan of keys, reducing the chances of them being exploited for unauthorized access or leading to data breaches. Essentially, even if a key is exposed, its usefulness for malicious purposes is significantly curtailed.
Incorporating key rotation into your security practices helps you proactively address potential vulnerabilities, safeguarding the integrity of sensitive data shared through your APIs.







